The goal of shipping software with zero bugs and vulnerabilities is an aspirational but unrealistic goal. Assuring your supply chain is up to date on the latest known issues and best practices is completely achievable. When new information is discovered, how fast can producers distribute, and consumers respond to newly discovered information?
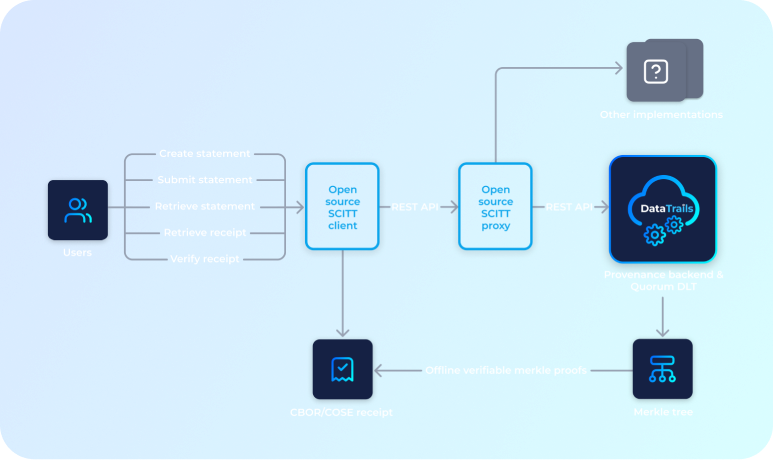
DataTrails is participating in building IETF standards and implementations to assure Supply Chains can be automated, being able to quickly identify whom said what about the artifacts business depend upon.

The Internet Engineering Task Force (IETF)
Was founded in 1986 and is the premiere standards development organization (SDO) for the Internet. The IETF makes voluntary standards that are often adopted by Internet users, network operators, and equipment vendors, and it thus helps shape the trajectory of the development of the Internet. Its mission is to produce high quality, relevant technical and engineering documents that influence the way people design, use, and manage the Internet in such a way as to make the Internet work better.
Being Accountable for Continued Change
The days of purchasing software, taking the time for humans to review each update before deploying, have long since passed. Updates from the myriad of dependencies companies take are frequent and from multiple sources. Updates are critical as updates are the mitigation and may be the source of new vulnerabilities. To keep up with an ever-changing digital world, humans must feed the machine without being bottlenecks in the workflow.
Being able to communicate this history of issues, and what mitigations are available, are critical parts of the supply chain, enabling humans to program the computers to make informed decisions. For automation to function securely, trust must be established in the production and consumption of all information.
It’s Not a Matter of If, Rather When
Two things are constant. Humans will make mistakes, and bad actors will exploit vulnerabilities. To react, producers and security companies must have a means to communicate what they learn about software that’s already been deployed. And consumers must have a means to consume the information from the entities they trust.
-
Trusted software producers & security companies
-
Information about vulnerabilities
-
Software consumers
Minimizing the Margins
The common tools available today create large blast radiuses. If a software component is viewed vulnerable, producers can revoke the signing key used to identify who distributed the software. The signing key represents the identity of the producer and may be used across entire product lines. Revoking a key can cause multiple products to fail deployments and may create a larger problem than the original exploit. Key revocation was intended for stolen identities, however as the primary tool (Hammer), all exploits become nails. Bad actors can exploit this behavior, leveraging a smaller exploit that creates a larger impact.
Producers and consumers need more granular means to communicate what issues apply to specific artifacts of a supply chain. Communicating details about specific software artifacts enables consumers to decide when and how to mitigate the issue, enabling more surgical accuracy, mitigating the blast radius an exploit would otherwise have.
Benefits
Surgical Accuracy
DataTrails implementation of SCITT enables producers and consumers to communicate more specific details for the components of a supply chain, leaving key revocation to be reserved for the less frequent identity and signing key theft.
Multi-Vendor Solutions
DataTrails builds upon, and is helping develop internet standards, enabling multiple vendors to communicate and interoperate. This gives producers and consumers the choice to work the multiple vendors and cloud providers they work with today.
Long Term Integrity
Be confident in audits years into the future with instant verification not only who did what when, but also who knew what when, with modern cryptographic underpinnings that only care about the actors back then, and doesn’t rely on them staying honest now.
Discover DataTrails for yourself
Achieve provenance, governance, and immutability for your supply chain data today.
Sign up and start securing your supply chain.